Included in the SSH specification is the hugely overlooked ability to tunnel traffic. Looking on the Synology forums and the Web in general I saw plenty of articles and blog posts on how to enable port forwarding on your router for all the various services these appliances can provide. Many of these services transmit their data in non-encrypted form, with passwords being sent in clear text. However, there is a better way – one that can allow you secure remote access to absolutely anything on your home LAN. I had used this method to connect to my hacked TiVo many years ago because its web interface didn’t have the option of SSL. I did find some Synology-specific info about it, but I suspect it was from much earlier DSM versions which perhaps didn’t have a decent SSH daemon, and so called for additional packages to be installed. I was sure that there must be a simple way to tweak the config of the existing daemon. Luckily I found this blog post which seems to be quite hard to find via Google.
UPDATE – no config changes are necessary, at least with DSM 3.2 onwards (can’t remember for 3.1).
The concept is simple. You connect via SSH with PuTTY, but in setting up the connection you define some port mappings. So let’s say you wanted to be able to remotely use the DSM software on TCP5000, you can define a local port of say 8500 and remap that to the private IP of your Synology NAS at home on port 5000 (so 192.168.1.202:5000 in my case):
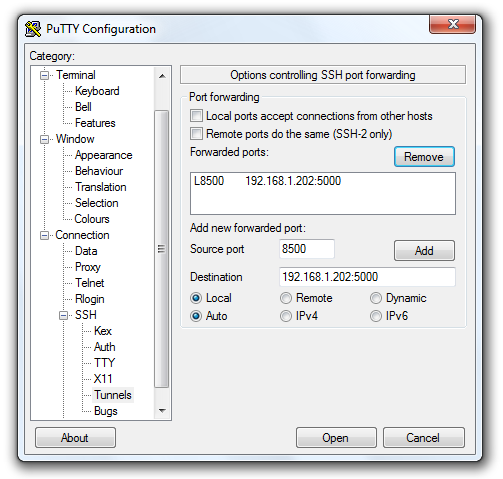
Don’t forget to click Add. Also in the options navigate to Window > Translation and set the character set to UTF-8.
Once you’re connected in PuTTY, point a browser to http://localhost:8500 and you’ll be connected to the DSM at the other end of the SSH tunnel – and securely too.
If you’re using a Mac or Linux computer the normal SSH client can be configured similarly from the terminal, e.g.:
ssh root@mynasip -L 8500:192.168.1.202:5000 -L 8123:192.168.1.202:8123
One final little mod is to enable coloured output in directory listings, and displaying of the current directory path in the shell prompt. Type:
echo alias ls="'ls --color'" >> ~/.profile echo export PS1="'\w\$ '" >> ~/.profile
This will take effect at next logon. Directories are blue, executables are green, and symbolic links are cyan.


could you please tell me how to revert this command to the previous state?
echo export PS1="'\w\$ '" >> ~/.profilethank you!
Edit the file ~/.profile and set that line back to the default value of:
PS1="`hostname`> "You can’t restart sshd while connected via SSH – so run the command from within a screen and it should come back up :)
I am getting a -ash: syntax error: unexpected newline after doing the echo export PS1 command; what do i do?
I would like to know how you actually create the SSH session and then set up Firefox socks5 setting?
How do you SFTP over SSH on a diskstation? SSH into the diskstation work find in putty and ubuntu, the SFTP is setup on the diskstation and works without an SSH tunnel, but i want both the the username and password encrypted (SSH), as well as the data (SFTP).
AFAICR you point your SFTP client at the Syno and use the admin account rather than root. Should work without any further config change I think.
Pingback: Beveiligde toegang tot de Synology DiskStation - ArjanWooning.nl